In this article, we'll cover:
Cloud security: A comprehensive guide for businesses
As businesses around the world take their operations to the cloud, the threat of cybercrime is growing substantially. According to a recent study, the global cost of cybercrime is expected to grow to a staggering $10.5 trillion by 2025.
Cloud computing is the present and future of business as we know it thanks to its flexibility, ease of scaling and reliability. But this also exposes the cloud to multiple internal and external security threats, including malware attacks, data breaches and other related security issues.
A secure cloud can help your company achieve everything from the digital transformation of your business operations to the storage of big data, and more. It’s imperative to safeguard cloud security to protect your data assets.

What is cloud security?
Cloud security, also known as cloud computing security, refers to a set of security measures that help protect cloud-based data, applications and cloud infrastructure from security threats.
More and more businesses across the world are using cloud computing in one form or another. In fact, the global cloud computing market generated over $360 billion in 2021.
The rapid shift to the cloud has raised concerns in IT circles regarding the cybersecurity of sensitive data being stored in the cloud. As cyber attacks get more sophisticated, companies are at a constant war footing to mitigate security risks and prevent data loss. It’s no longer enough to invest in a firewall, sit back and relax (if it ever was).
Maintaining a robust cloud security system is crucial to ensure data security and optimise the many benefits of cloud services, including lower upfront costs, ease of scaling, reduced admin and operational costs and higher reliability.
There are three main cloud environments—public, private, and hybrid cloud. Public clouds are hosted by third-party cloud service providers (CSPs). Such CSPs include Amazon Web Services (AWS), Microsoft Azure and Google Cloud Platform (GCP).
Private clouds provide cloud infrastructure to a specific customer or business. Because of the limited access provided by private clouds, they are necessarily more secure and have greater security controls.
Hybrid cloud is a mix of public and private cloud models. It offers the best of both worlds for a business. For example, a company can leverage the low cost of public cloud for low-risk activities like instant messaging, but reserve a private cloud to store more sensitive data.
Different types of cloud security responsibilities
Cloud security follows a “Shared Responsibility Model” between the cloud service providers and the end-user.
The CSP is usually responsible for issues that threaten the cloud infrastructure. The customers or cloud users on the other hand, undertake security responsibility for any data they store on the cloud, to protect it against possible data breaches. This shared responsibility does place a significant onus on users, however, with mixed results as revealed by recent Gartner research:
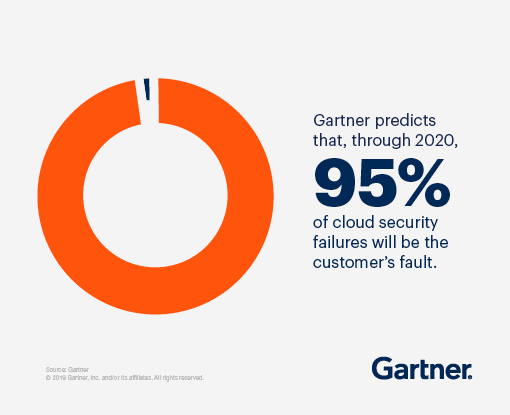
Customers should always be sure of which security responsibilities are being handled by CSPs and which ones they have to undertake on their end. Cloud security responsibilities vary by the service model.
Platform as a Service (PaaS)
PaaS cloud services provide end users with a dedicated platform to develop their own applications. Cloud service providers manage the runtime, middleware, and operating system. Customers are responsible for managing their data, applications, user access, and end-user networks. PaaS examples include Windows Azure and Google App Engine.
Infrastructure as a Service (IaaS)
IaaS cloud services provide both the hardware and the remote connectivity frameworks to support the majority of computing services, including the operating system.
CSPs only manage core cloud services. The end users are responsible for the security of all applications, data, and runtimes that are stacked onto the operating system. Popular IaaS examples include Amazon Web Services (AWS), Microsoft Azure, and Google Compute Engine (GCE).
Software as a Service (SaaS)
SaaS cloud services provide access to applications that are hosted exclusively on the cloud service provider’s servers. The CSPs manage all data, runtime, and the operating system. Popular SaaS products include Microsoft 365, Google Drive, and Salesforce.
Cloud security features
Keeps data secure
One of the primary objectives of cloud security is data protection by mitigating threats. A cloud security solution will include tools to implement barriers between the visibility and access points for sensitive data.
Encryption is one of the most effective security tools. It scrambles data so that it’s only readable by someone who has the encryption key. So any encrypted data that is lost or stolen before it reaches its desired endpoint will be essentially useless to the finder.
Uses policy-based identity and access management controls
Identity and access management (IAM) controls refer to the accessibility privileges offered to users.
This also includes managing authentication and authorisation of user accounts. Access controls enforce restrictions on who can access the data, thereby preventing data breaches. Multi-factor authentication and password management fall in the scope of IAM.
Its own governance and policies aim to prevent, detect, and mitigate threats
Cloud governance deals with security policies for identifying, preventing, and mitigating threats. Early threat detection can help businesses track and prioritise threats to maintain network security and minimise damage.
Visibility, control, and access to cloud data & applications
Cloud security provides consolidated visibility and access to cloud data, security policies, and configuration settings, in addition to hidden risks in online data stores. This reduces the chances of missing any weaknesses in your cloud security due to misconfiguration.
Legally compliant
Data privacy laws and compliance requirements are now stricter than ever, so any company that is dealing with sensitive client data needs to ensure they are complying with the right regulations (GDPR, for instance, if you’re serving customers in the EU). Data masking is commonly used by companies to obscure identities within data.
Segmentation of different services and tenants
This entails using varied multi-cloud environments, cloud accounts, virtual private clouds (VPCs), and roles for different types of workloads.
Cloud security challenges
Despite its many benefits, cloud security also faces some challenges:
Internal threats
A 2020 Cost of A Data Breach Report by IBM mentions that 23% of breaches are caused by human error. It could be a dishonest or simply negligent employee who could knowingly or unknowingly expose a company’s cloud data to security threats.
Companies should train employees about data security so they can be held accountable in case of a violation. Stringent data encryption measures can be put in place in data centres to prevent unauthorised access. It should also be recognised that on-premises infrastructure is by no means immune to human error, either.
Cloud compliance and governance
Cloud services are bound by an obligation to regulatory compliance and governance. Most cloud computing environments need to follow regulatory requirements like PCI and HIPAA, in addition to regulations from internal teams, partners, and customers.
DDoS attacks, malware, phishing, and other cybersecurity threats
Distributed Denial of Service (DDoS) attacks typically stream large volumes of traffic to a web server, preventing it from responding to legitimate requests. Cloud computing is based on shared distributed computing resources, making DDoS more complex and difficult to detect and prevent.
Malware and phishing are among a host of other cybersecurity threats that can target cloud environments and compromise sensitive data.
APIs lacking security
Application program user interfaces (APIs) are the most common way to operate and integrate cloud systems. APIs can be used by internal business employees and externally by customers, via mobile or web applications.
APIs can provide several types of data, including sensitive data that can be valuable to attackers. APIs are publicly available and their inner workings are well documented, making them a key target for cyber criminals.
Misconfigurations
Avoidance of cloud-native breaches is usually the cloud customer’s security responsibility, which includes the configuration of the cloud service. Misconfiguration of IaaS often leads to a cloud-native breach, allowing the attacker to exfiltrate data.
Complex environment and multi-tenancy issues
With cloud computing, everything from the core operating system and infrastructure to single files can be accessed remotely 24/7. Cloud storage can place all of this data on the servers of a handful of service providers, thus exposing it to security threats. Hackers can target the data centres of these large service providers and cause severe data breaches.
Cloud security best practices
Manage your passwords, devices, and authentications regularly
You should try to assign different passwords and authentications to each application, service,or database that you access. Whilst choosing your password, include a combination of alphanumeric and special characters. Remember to protect your password manager with a strong primary password.
Run intermittent data backups & continuous cloud monitoring
It is good practice to regularly backup all your data so that in the unfortunate event of a breach or system outage at your cloud provider, your data can be fully restored. The backup could be on your personal device, an external hard drive, or even cloud-to-cloud, as long as the two service providers don’t share infrastructure.
Establish strong policies on access and permissions
It’s important to establish strong policies on who has access to your data. Implement a strong Identity and Access Management (IAM) policy to control who gets access. Use the principle of least privilege (POLP) and require multi-factor authentication.
Research and study the responsibilities & agreements with your CSP provider
Remember to do your due diligence before choosing your CSP. You should be aware of the security controls they offer, and review contracts and service-level agreements (SLAs). You also need to understand the shared responsibility model, including the different responsibilities of your CSPs and your security team.

What to look for in a cloud service provider
Regular security audits & integrated security
It’s important for service providers to conduct regular security audits of their cloud configurations to ensure all systems are secure and no accidental modifications have been done. These audits can be performed with a variety of tools and processes, including automated scanners and manual audits.
Capable to logically segment and separate important data
Data loss is a common occurrence in a cloud environment. This is because a single error can effectively wipe out large volumes of data in a single go. To avoid this scenario, it’s crucial to segment and separate important files and data.
Set up archiving for large amounts of data that’s not used frequently, and can be separated from production workloads. Use backup to keep copies of your data in different remote locations. Use recovery to set up automated disaster recovery, for quick recovery of lost data after a data breach.
Requiring strong authentication for a more secure cloud
A good cloud security services provider can offer strong authentication measures. These regulate access control through strong password management and multi-factor authentication (MFA). Multi-factor authentication should be supported for both internal and external users.
Updated with relevant policies and should be continuously compliant
Cloud systems must be regularly updated with relevant policies so they’re not unwittingly exposed to vulnerabilities. This is particularly relevant for any unresolved vulnerabilities. An attacker will likely know about these vulnerabilities on your system and how to exploit them.
Some cloud management systems only require you to accept updates and patches. In other cases, you will have to create your own patch to resolve a specific vulnerability. Automated tools can continuously verify that all software systems are running the latest version.
Visible and braced for threat detection
System administrators have a centralised view of all user activity, and of all internally and externally shared content. Cloud security providers use machine learning to track suspicious
activity and generate alerts. For example, data behaviour analysis might identify a member of your sales team trying to access confidential reports.
Is your business equipped with cloud security?
It’s crucial to do a thorough audit of your existing security measures to find out if your business is properly equipped with cloud security. The importance of safeguarding your cloud security can’t be overstated. It is what separates the successful running of business from disaster.
Originally published Oct 06, 2021

