In this article, we'll cover:
What is eavesdropping?
Eavesdropping is the act of listening to someone else’s private conversation. Deriving from the literal history of the term, the practice of actually standing beneath the eaves of a house to deliberately overhear a private conversation inside, virtual eavesdropping has become a common threat to corporate privacy and security digital age.
Eavesdropping in IT security
In the IT security sense, eavesdropping refers to the unauthorised and unseen intervention of a private, live conversation. Eavesdroppers can intercept a phone call, video call, instant message and even fax transmissions to acquire sensitive or desirable information and data.
In recent years, increasing usage of VoIP systems and IP-based calls have made businesses susceptible to eavesdropping attacks. With VoIP systems that lack encryption, communications are easier to intercept than with TDM-based phone calls. Hackers can choose and record calls without being detected by any other participant on the call.
While a lack of encryption can make your data and information vulnerable, even systems that use encryption can be insufficient in protecting against eavesdropping attacks.
Using specialised software and cryptographic tools, hackers can easily convert digital voice files from standard CODECs into audio files. PCs and other devices have microphones built-in. These can be enabled as listening tools without the awareness of the device owner.
Likewise, the speakerphone function on IP phones can make businesses vulnerable to interception. It can be activated remotely, allowing hackers to listen in to an entire office without the inhabitant’s knowledge.
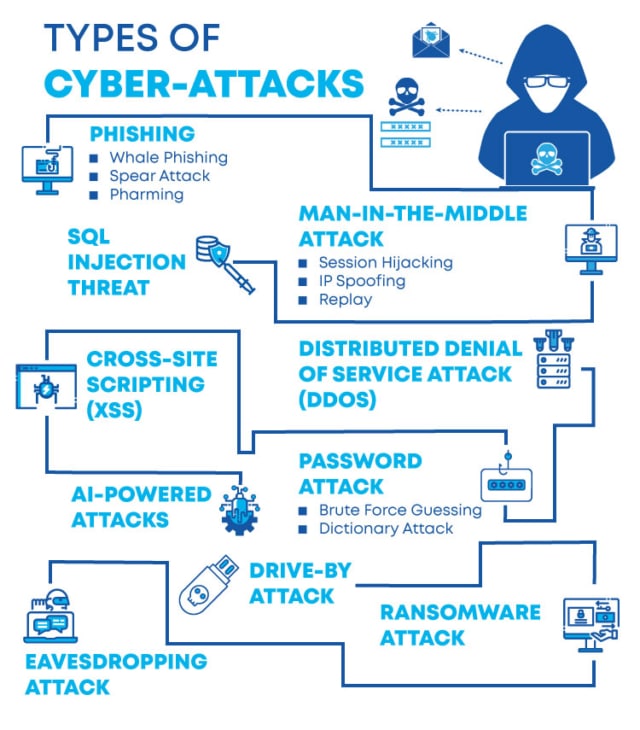
Types of eavesdropping attacks
Technical eavesdropping on a traditional telephone line was known as wiretapping. Since then, methods of eavesdropping have become even more advanced. In tandem with developments in technology, hackers have had the chance to cultivate new methods and channels for eavesdropping on digital conversations. Protocol analysers can be used to record IP-based communications and can convert data into easily accessible audio files.
Data sniffing is another common type of electronic eavesdropping. This method is mostly used to target businesses using local networks. As all communications within the network are sent to the network ports, hackers can tap into the system and intercept incoming data. Similarly, wireless networking data can be easily manipulated if unsecured information reaches the network ports.
Arguably, the most common form of eavesdropping is conducted using a device’s speaker function or microphone. This type of eavesdropping attack most commonly occurs via a user’s laptop, as the microphone can be activated discretely and remotely by a third party.

Preventing eavesdropping and protecting privacy in virtual meetings
As video calls and video conference calls increasingly become the norm as part of a remote or hybrid working routine, paying attention to cyber risks is paramount.
While many IT teams have become more conscious of the security of our online communications, colleagues conducting virtual meetings daily may still neglect the importance of security, meaning video calls have particularly become a targeted weak spot for eavesdroppers.
Many of us have experienced the video call where another participant enters the virtual room before the previous meeting. Reusing the same access code makes your video calls vulnerable, as you’ll have shared that code with a large number of people, meaning it could easily get into the wrong hands. If calls are not set up correctly, former employees, hackers, or current staff members with a vendetta could effortlessly eavesdrop or intercept them.

Mitigating the threat of eavesdropping attacks calls for some factors and new approaches to drive better privacy in virtual meetings. Here are a few of the best ways you can advocate more secure meetings:
1. Encourage more widespread awareness:
There is still a knowledge gap in terms of security. Without proper education, many employees may not see or understand the real impact of a possible security break, so raising awareness is crucial to get your workforce on board with any new security regulations.
IT managers need to educate staff and demonstrate good practice to help overcome the dangers of cybercrime. In an increasingly remote working world, it’s important to encourage employees to think more carefully about the apps they use and, more importantly, where they use them.
2. Use platforms with stronger encryption credentials:
Encryption is the process of encoding information, allowing you to disguise sensitive information. Used as an essential and widespread way to protect your data over the internet, encryption offers the best defence against potential eavesdropping attacks.
When the video has become a core communications channel, security must be front of mind for all those using the software. Some platforms do not use encryption if it can hinder performance, so be sure to opt for a solution that prioritises your security.
Choosing a video platform that uses strong encryption means you’ll make it easier to protect your privacy and data and far harder for any eavesdropper to attack.
3. Advocate better network access controls:
Practising better control over who can access your network can also help you mitigate cybercrime challenges. In many cases, all a hacker might need to access your network is access to the physical building. Thinking carefully about the location of your network or WiFi points around the building is important. Whether those points might make you vulnerable to cyber abuse, and if so, make a plan for some better physical security measures.
Likewise, if your network is wireless, it could be even easier to abuse. Adopting better network access control, or NAC means you can block unauthorised devices from being able to connect to your network altogether, only allowing known and trusted devices to access. This makes it much more difficult to infiltrate the system and means any potential attacker will think twice before choosing your business as a possible target.
Arguably, the most powerful way to prevent security breaches in day-to-day meetings is to instil better habits within every team member. With better awareness, IT departments can make this easier by simply enforcing more stringent regulations and processes around conducting virtual meetings.

How to conduct safer virtual meetings:
- Avoid reusing your access codes. If you always use the same access code for your virtual meetings, more people likely have access to your virtual meeting room than you’d imagine.
- If your meeting content is sensitive or thinks confidential information might be shared, try to use a unique PIN. Depending on your provider, extra authentication methods might be available to you and help safeguard your meeting.
- Make use of the ‘waiting room’ feature within your communications tool. That way, you can keep control over when the meeting begins and ensure only the invited, authorised participants can enter the room.
- Lock your virtual meeting room once your participants are present. This makes it much more difficult for any uninvited guests to attend.
- If you have generic attendees, ensure that the host politely asks that they identify themselves. Depending on your provider, notifications can be set up to announce your attendees’ names as they enter the virtual room.
- Set restrictions on which participants can share their screen. If you are using the screen sharing function, make sure participants are reminded not to share any tabs with sensitive data or information.
- Think carefully about whether you need to record your meeting. While the record function can be handy, it also makes it easy for your meeting content to get into the wrong hands.
- Follow an official process and adhere to the organisation’s policies when conducting any virtual meeting. A print-out or crib-sheet with step-by-step instructions outlining each protocol’s reasons (such as the above) can help employees educate themselves and enable the highest possible security levels for their meetings.
While the above is not an exhaustive list, all employees need to know the risks and understand how your day-to-day tools might mitigate them. Getting comfortable using your collaboration tools’ various features and functions is crucial for working remotely; using them wisely is imperative when it comes to keeping your business secure.
How is RingCentral providing security in its services?
As a result of the COVID-19 pandemic, businesses need failsafe security now more than ever. That means it’s more important than ever to appoint vendors that prioritise security as high as you do.
RingCentral’s robust, reliable solutions are designed with security at the core. Our services are hosted globally in tier 4 enterprise-class data centres and leading public clouds. These environments boast cutting edge physical security, facility operations and environmental controls.
Our easy-to-use collaboration platform offers a range of features, including identity access management, multi-factor access controls to help alleviate risks, and our dedicated cybersecurity experts offer support to implement the following measures:
- Secure software development
- Strong access controls
- Resilient services
- Threat detection and mitigation
- Service operations controls
- Customer admin and user controls
- Built-in support for regulatory requirements
- Secure application programming interfaces (APIs)
- Pre-built integrations
- Transparency
Our team is committed to providing businesses with the highest level of security, data confidentiality, compliance, control, and availability. Combining a robust back-end infrastructure with a dedicated, global security team, RingCentral guides customers to ensure that your data and communications are defended at every touchpoint.
Get details on the security and trust built into RingCentral products and services.Download the white paper
Originally published Apr 20, 2021, updated May 15, 2021

