In this article, we'll cover:
The data sent over computer networks (for example, over the internet or ethernet by a VoIP phone system) is broken down into packets—or small segments of messages. These packets get re-combined when the destination device or computer receives them.
What is a network packet?
To more clearly define a packet, here’s an imaginary example:
A writes a relatively long letter to B, but B’s mail slot is big enough to accept small index cards. To make sure B gets their letter, A divides the letter into shorter, smaller sections (sized to fit through B’s mailbox) and delivers these cards to B. B can then put them in the right order to make the entire message readable.
Packets on the internet work in a similar fashion. When a user wants to upload an image, for example, the image file doesn’t go from a web server to that user’s computer in its entirety. It’s broken down into “packets” of data sent via wires, cables, and internet radio waves to be reassembled by the user’s device into the desired image.
Everything that happens on the internet involves packets—from web pages and digital telecommunications to emails.
What is a packet-switched network?
The internet uses a packet-switching network. Packet switching transmits data efficiently across digital networks by allowing network devices to process packets separately.
When one device sends data to another, the file is broken down into packets which can then take different network paths towards the same destination, with the proviso that all of them arrive at the same place. Packets may have to arrive in the right order, even though they each take a different route to reach their destination.
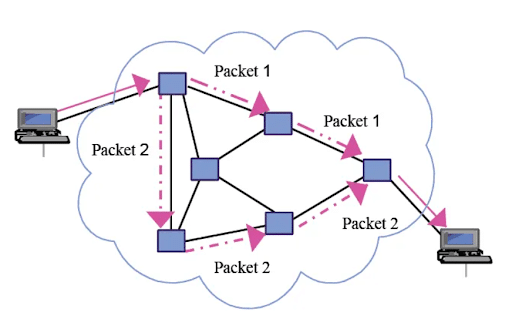
Packet switching functionality enables packets from multiple computers to travel over the same wires in any order—routing them so connections can occur over the same equipment simultaneously. This means that billions of devices can use packets to exchange data over the internet simultaneously, rather than just a handful.
Sending an email via packet switching
Let’s look at an example of packet switching:
When an email message is sent, a request is sent on the internet via Hypertext Markup Language (HTML), Graphics, Uniform Resource Locator, or Interchange Format.
The Transmission Control Protocols of the internet (TCP/TCP/IP) divide the file into bytes or small chunks of information to enable efficient routing. A “byte” or email packet typically holds one to one and a half thousand bytes of information to enable them to get to their destination—data including:
- The sender’s IP address
- The recipient’s IP address
- Information about how many packets of information the email has been broken down into
- The number of this specific package.
Individual packets for a given file can take different routes over the internet. Once they arrive, they’re re-packaged into the original file by the TCP layer that receives them.
Why use packets?
In theory, it could be possible to send data and files of a fixed length over the internet without breaking them down into smaller pieces. One computer could send data to another in the form of a long string of unbroken bits (units of pulsed electricity that computers can understand).
This approach, however, is not practical if more than two computers are involved. The long line of bits that pass over the wires between two data centres is connected so that no third-party computer could use those same wires to send information. The additional computer would have to wait in line for its turn.
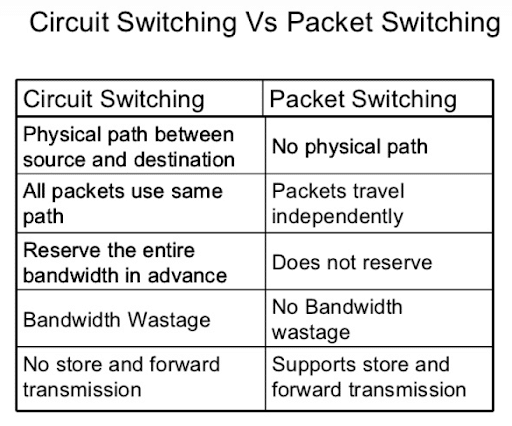
The following table shows the benefits of packet switching as opposed to circuit switching:
How does a network packet work?
Every network packet or unit of data is sent to its destination address using the best route available. This is a route taken by all the other packets within a message or by none of them.
This makes the network more efficient, balancing a load across multiple pieces of equipment from millisecond to millisecond.
If there’s a problem with one item of network equipment during the transmission of a message, packets can be redirected using routers to ensure the entire message gets delivered.
Depending on the network being used, packets can also be referred to as:
- Frames
- Blocks
- Cells
- Segments
Network packet structure
Network packets have a header and a payload. The header contains information about the packet, such as its origin/destination IP address. The payload refers to the “actual” data being transferred. For example, with a photo, the packets making up the image have a payload, each payload carrying a small piece of the image.
Packet headers go at the front of packets so that routers, switches, and computers (or anything that receives and processes packets) will see them first. Packets can also have trailers and footers at their end. Like headers, these contain information about the packets.
Not all network protocols attach trailers and footers to packets. In fact, the majority only attach headers.
What is a packet header?
A packet header is like a “label” and provides information about a packet’s content, origin, and destination.
Again let’s look at an example.
As in the previous scenario, when A puts the index cards through B’s mailbox, B isn’t given enough context to read the entire message.
So, A needs to indicate the correct order in which the cards should be read. A must also tell B that every card is from A—if B receives messages from other sources while A delivers their message. To help make things clearer, on the first card, A could write “Letter from A, 1 of 15”, and on the second card, A writes “Letter from A, 2 of 15”, and so on.
A can create headers, in miniature, on the cards so that B doesn’t lose them or get them mixed up.
In the same way, all computer network packets have a header to serve the same purpose.
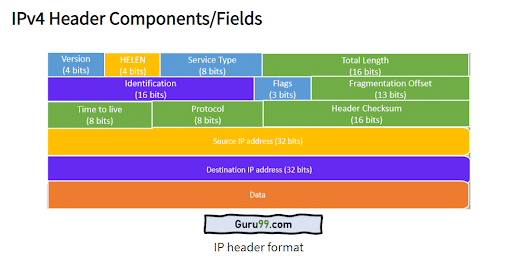
In fact, packets have more than one header, each used by a different aspect of the networking process. Packet headers are attached via certain kinds of networking protocols.
Internet protocols provide a standardised way of formatting data so all computers can interpret the data. There are multiple network protocols responsible for interpreting data, and some of them add headers to packets with information associated with that protocol.
At the very least, most packets traversing the internet include a Transmission Control Protocol (TCP) header and Internet Protocol (IP) header.
UDP (User Datagram Protocol) is another protocol often used for applications that frequently undergo packet loss—e.g., for streaming audio and video.
What is an IP packet?
Internet Protocol (IP) is a network layer protocol that’s involved in routing. It’s used to ensure packets arrive at their correct destinations. A packet with an IP header is sometimes referred to as an “IP packet”.
The header contains information about where a packet derives from (its source address), where it’s going (destination IP address), the size of the packet, and for how long network routers need to continue to forward the packet before it is dropped.
What is network traffic? What is malicious network traffic?
Network traffic refers to the packets passing through a network; in the same way, vehicular traffic refers to the cars and lorries that travel on roads.
However, not all packets are useful and not all network traffic is safe. Unfortunately, attackers can create malicious network traffic with data packets that can compromise an entire network. This could result in a distributed denial-of-service (DDoS) attack, vulnerability exploitation, or another kind of cyber attack.
One of the biggest FAQs for businesses, particularly when employees are working and meeting remotely, is how secure their data and information is and how high the quality of service is.
RingCentral Quality of Service (QoS)
Some platforms have known vulnerabilities, but not RingCentral. RingCentral products protect users from malicious network traffic, keeping data secure by employing encryption. This means all RingCentral hosted meetings are fully protected. Users also have the ability to configure their security settings exactly as they want.
RingCentral Quality of Service (QoS) analytics provides information about the global health of phone and video services. This means that problems—for example, bandwidth—can be monitored and potential issues addressed immediately. Thus ensuring not only the safety, but the quality of calls remains high at all times.
It’s easy to host an online meeting with RingCentral from any device without even downloading a mobile or desktop app. As part of a unified connectionless network system, RingCentral users can access enterprise-level VoIP without installing any expensive hardware since everything happens online.
Visit the RingCentral website to learn more about how to scale up your operations safely and productively and work from anywhere.
Originally published Aug 18, 2021

