In this article, we'll cover:
Security Development Lifecycle 101: Overview, Phases, & Benefits
When we talk about security in software development, typically we’re talking about whether or not the software product being developed is “secure”. When a piece of software is described as secure, people expect it to be trustworthy, free from obvious defects that would make it vulnerable to attack, and able to serve its function without unnecessarily leaking users’ personal data.
In the field of software engineering, a security-first approach to the software development lifecycle is known as a security development lifecycle.
What is a Security Development Lifecycle?
A security development lifecycle (SDL) is one in which this kind of information security is considered at every stage of software development.
Modern software users demand privacy and the peace of mind that comes from knowing their sensitive information can’t be stolen and they won’t fall victim to fraud or data breaches.
Rather than treating this requirement as an afterthought, a security development lifecycle builds in security features from the ground up. It doesn’t think of software security as an extra layer to be added to a product prior to release, but as one of the foundational design principles of building good software.
The contemporary approach to security-focused software development owes much to the Microsoft security development lifecycle. Since 2004, Microsoft has made building security into its software using SDL protocols a standard.
As a result of its success at releasing more secure products, and because it has shared many of its SDL materials and tools as open source, the Microsoft model has since gone on to represent many security best practices for software developers.
Phases of the Software Development Lifecycle (SDLC)
While development teams use a number of different methodologies in the process of building software, such as Waterfall, Iterative, or Agile, all these are typically composed of six phases which are carried out in a cyclical fashion.
1. Planning and Requirements

This phase of the SDLC is where objectives, goals, and team responsibilities are set. It’s in the planning phase that the purpose of the development project is articulated and the metrics by which success will be measured are defined.
2. Architecture and Design
The architecture and design phase of development portrays a more detailed blueprint of the end product. It helps to specify the basic components of an application as well as design the basic architecture.
3. Test Planning
During test planning, a testing methodology is proposed that will be used to measure and test the performance of the software once coded.
4. Coding
Often the longest phase of the SDLC, the coding phase is when the actual source code that a piece of software is composed of is written.
5. Testing and Results
Once a project has a functioning application, this is then tested using the framework specified at the test planning phase.
6. Release and Maintenance
Once a piece of software is developed, tested, and deemed ready for deployment, it can be released to end-users. In continuous integration and delivery models, maintenance is performed on an ongoing basis with regular updates and patches being released either routinely or as needed.
This development process is known as a lifecycle to distinguish it from linear development models. This means that as long as a project is still being worked on by developers, the cycle can continue indefinitely.
In less secure SDLCs, developers tend to only perform security-related tasks at the testing stage. A core value of the security development lifecycle is that security requirements are considered during every phase of the SDLC.
How to Get Started in SDL
If you want to start developing more secure software, you’ve probably already decided that implementing a SDL is the best way to go about it. But with six phases of software development to consider, where do you start?

Follow these four steps and you’ll be equipped with the basic tools to start implementing secure design throughout the SDLC.
1. Educate yourself and co-workers on the best secure coding practices and available frameworks for security
Start by educating all the members of the software development team on the principles of secure design. Choose a security-oriented DevOps framework you wish to apply and make sure all team members understand the specific security concerns of the project.
2. Conduct an architecture risk analysis at the start
An architecture risk analysis is a risk assessment and threat modelling tool for secure software development. It considers who the end-users of the software will be, what kind of information assets the software will deal with, and identifies potential security risks and attack surfaces that will need to be taken into account during the design phase and throughout the SDLC.
3. Consider security when planning and building for test cases
A secure testing strategy requires test objectives that focus on cybersecurity. Security testing doesn’t have to compete with functional or usability testing, but should be seen as complementary to other test objectives.
4. Use code scanning tools for static analysis, dynamic analysis, and interactive application security testing
Code scanning tools can be applied throughout the SDLC to ensure your source code is free from exploitable flaws. Interactive application security testing (IAST) analyses code for security vulnerabilities while the app is being run.
IAST is useful as it reports vulnerabilities in real-time, which means it doesn’t add extra time to your development pipeline.
Security Testing Activities
Although a SDL differs from less secure SDLC frameworks by removing the need to find security issues from the testing stage alone, this doesn’t mean that testing isn’t important in a SDL.
Instead, think of a SDL as one in which the testing phase is applied throughout software development, as opposed to being reserved for a one-off code review prior to release.
To minimise the number of security vulnerabilities that slip under the radar, you should apply multiple test types and testing frameworks.
Static Analysis
Static analysis identifies the exact location of weaknesses by analysing the software source code without executing it.
Dynamic Analysis
Dynamic analysis identifies weaknesses by running the software. It integrates testing, bug reporting, and vulnerability mitigation.
Vulnerability Scanning
Vulnerability scanning purposely injects software with malicious inputs to check how the program reacts. For example, vulnerability scanning can be used to test the resilience of a piece of software to SQL injection and other common attack vectors
Fuzzing
Fuzzing or fuzz testing is an automated software testing technique that inputs invalid, unexpected, or random data into an application. The application is then monitored for undesirable reactions such as crashes or memory leaks.
Third-Party Penetration Testing
Third-party penetration testing involves enlisting the help of testers from outside the development team to simulate attacks a program might encounter from malicious agents.
External audits increase security awareness by providing a fresh perspective and remediating the tunnel vision that development teams can fall victim to.
Benefits of Adopting a Secure SDLC
Adopting a secure SDLC has benefits for a software project’s various stakeholders, including software engineers, financial backers, and end-users.
Makes security a continuous concern
Adopting a SDL makes developing a secure product one of the primary goals of the SDLC. Instead of designating this responsibility to a dedicated security team, a SDL uses security-oriented metrics to measure performance at each phase of development.

Helps detect flaws early in the development process
Because a SDL incorporates verification and validation into every phase of development, it helps development teams detect flaws early on.
This can prevent bad code from being embedded in a piece of software, which can make problems difficult to remediate once a project has grown in complexity.
Reduces costs
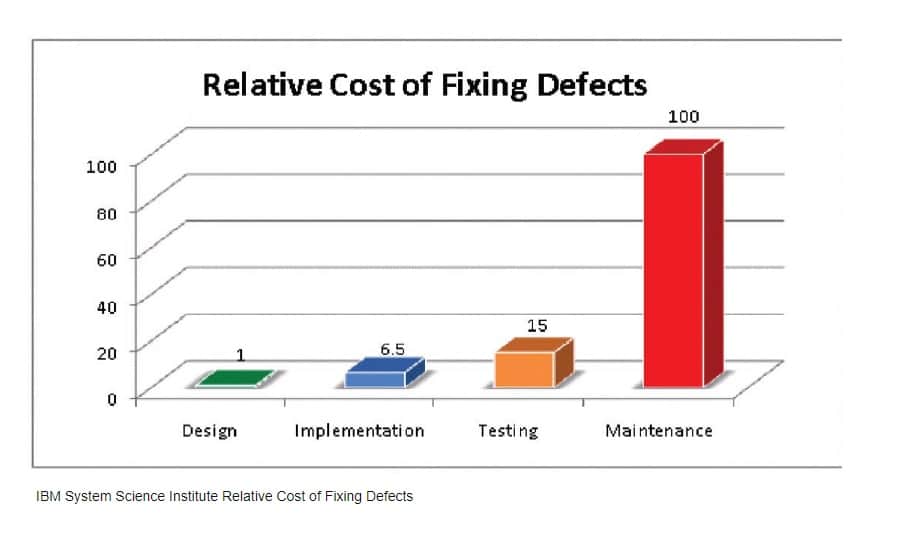
Research by the IBM System Science Institute has found that integrating secure coding practices into the overall SDLC can save software developers significant expenditure. That’s because it costs up to a hundred times more to fix a bug found during maintenance than one identified during design.
Learn All About the Security Development at RingCentral
RingCentral implements a security development lifecycle in all its software releases. As a leader in the field of cybersecurity awareness for businesses, we also champion the SDL approach for all users of our services.
In line with the security-focused software development paradigm discussed here, the
RingCentral product development process includes a security review every step of the way—from concept to release. What’s more, we employ qualified, independent third-party auditors to perform security audits throughout our SDLC.
Because we have built security into our products from the ground up, RingCentral’s unified communications solution, RingCentral MVPTM, has achieved ISO 27001, ISO 27017, and ISO 27018 certification for information security best practices.
As a cloud service provider, RingCentral is also always looking for ways to enhance security within the field of cloud computing.
As such, we support the use of the German verification framework known as C5, which stands for Cloud, Computing, Compliance, Controls, and Catalog. RingCentral is fully C5 certified and recognises the C5 attestation as a rigorous standard for security-focused development in the cloud sector.
Originally published Feb 07, 2022

